How I unsuccessfully, then successfully flashed the BIOS on my Purism laptop from Coreboot to Heads.
I’m not the most tech savvy person in the world, but probably know a little more than most…one thing I do have an abundance of is curiosity. Curiosity killed the cat and it nearly killed my new computer. I cannot help myself. I get something new, and I just have to dig, strip it back and see what it can do. The worst part is that generally I have no idea what I am doing, other than I’m going to do it. It is something I only do with tech…the way it comes is never how I intend to use it.
Earlier this week I received my Purism laptop (v4) and it did not disappoint. I love the security features (hard wired kill switches for radios and webcams), but most of all I just love the ethos of Purism, so was happy to pony up the dollars for their bit of hardware (my review is in the hardware section and coming later). Of course, me being me, simply getting the laptop and using it was not enough. Sure I booted it up, and had a brief look at their PureOS operating system, but for me it was about Qubes…so installed that straight away! Qubes is good, so secure, so interesting, and is really up my alley; perhaps not just now. I am typing this from PureOS, and I’ll explain how and why I am back here on their native OS.
What was up my alley most of all was the Purism Librem key, which is the security device to test if the BIOS has been tampered with. Now, don’t get me wrong, my BIOS is not going to be tampered with. People I know just wouldn’t know what a BIOS is let alone how to flash it, or tamper with it. It was the idea of this added level of security that had me most intrigued and I just had to get it, test it out, and get it working.
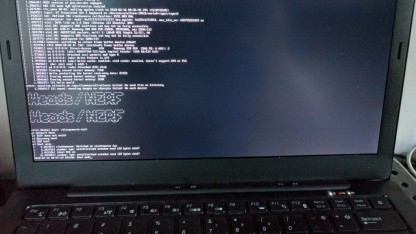
Unfortunately Qubes and the Lbrem Key do not seem to work together too well, but me being me, I’ll be testing it out, and will let you know what I break. As I now have Heads boot working, I cannot see why I now cannot install Qubes, as the Librem key tests the BIOS not the operating system (as that is why we have LUKS encryption and passwords, in addition to malware procedures).
In order to get the Librem Key to work, I had to reinstall PureOS; which of course is super easy, as I just flashed the free ISO and away I went. One thing I had never done before was changing the BIOS, but thankfully the team at Purism make this easy with just a little shell script. Of course, yours truly still raced ahead, and as a result at the close of the night was left with a blinking screen not doing a great deal and a new computer that I feared was going to become a very dear paper weight…time to call it a night.
Thankfully the next morning I was able to get an OS up and going from a USB and that at least gave me an interface to get somethings back on line. With a bit of extra effort I was able to get the Librem Key working, and Heads BIOS talking correctly to the key.
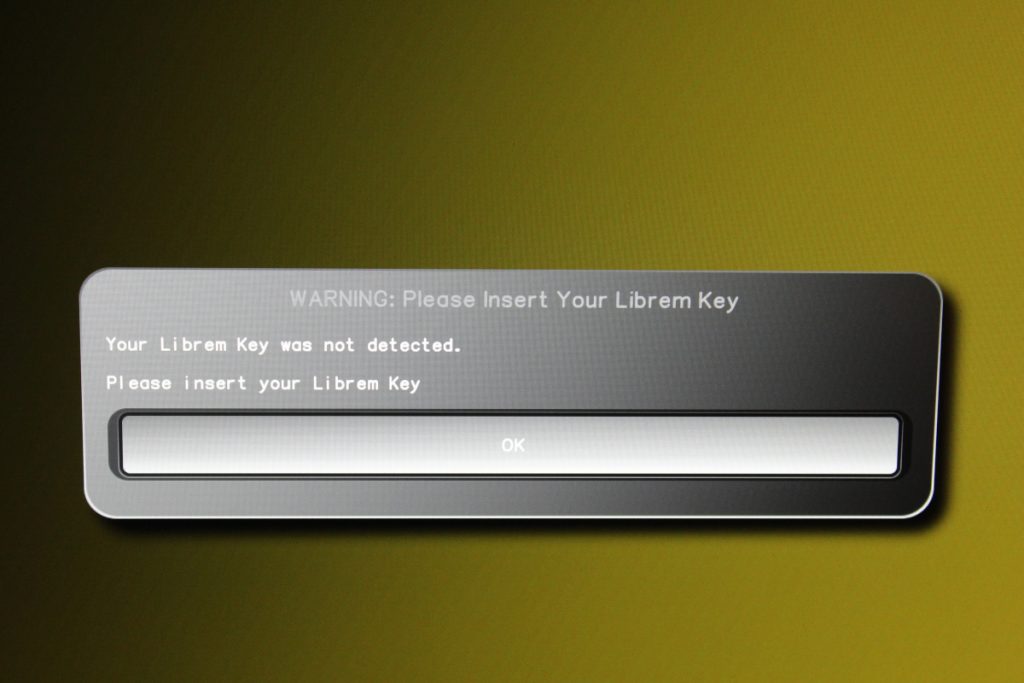
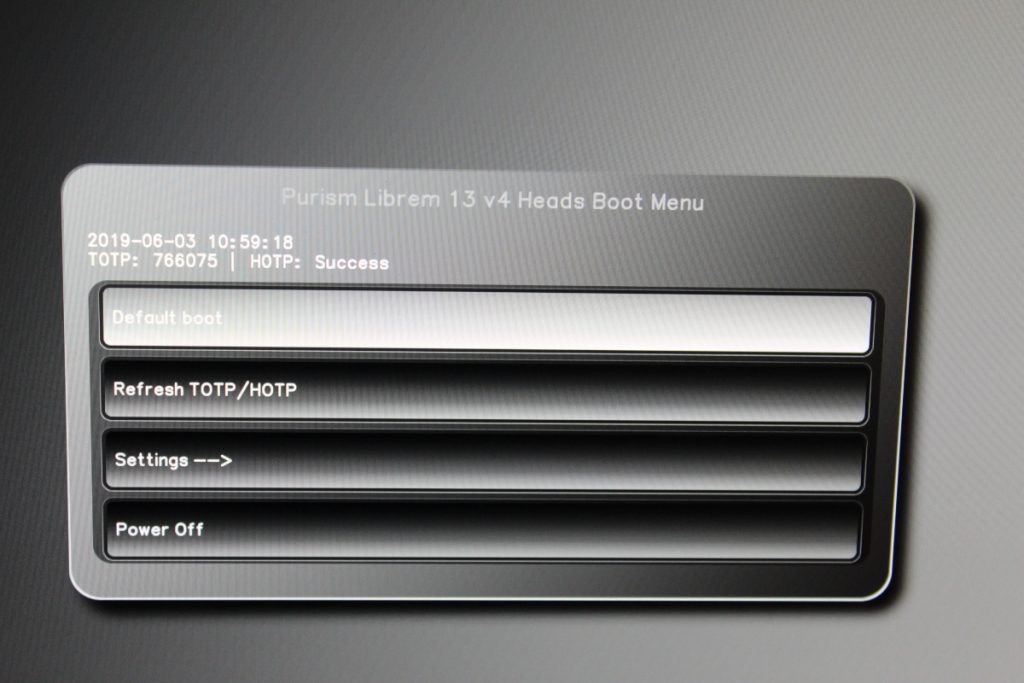
Getting these tools working and being able to test out the hardware (and PureOS, I guess) is enough for me now. I really want to see what this Purism laptop can do, which so far seems a very powerful and well built device. I really do not have any complaints with anything, and I must admit that I was especially impressed how every component of the laptop shipped in individual vacuum sealed bags, so I could be certain that my device was not tampered with at all at customs. Of course, changing the OS and BIOS has me guaranteed to be operating from a cleanskin device.
Ultimately I think what Purism have developed are a suite of fantastic products that really embrace the FLOSS philosophy; these are products I’ll continue to use, and see if I can break…starting with getting Qubes to work with Heads.
My curiosity will never end, as I commence my journey of cybersecurity education, I can at least now add a new skill to my repertoire, I can flash a BIOS…well sort of. Getting close to bricking the computer was not a pleasant experience, but being able to troubleshoot my way out of it, all without engaging tech support was a very liberating experience, and I’ve definitely learned a few more skills.
Lessons Learned
- Appreciate the readme.txt files and resources much smarter people than me have left behind.
- Slow down! It is not a race and missing a step can have catastrophic consequences.
- Always have multiple computers and storage devices available (thankfully I did)
Positives
- Command line skills definitely improved as a result of this exercise.
- In the face of a bricked computer I was able to troubleshoot my way out of it.
- Have a better understanding of computer softwares and their relationship to computer hardware.
Negatives
- Probably more luck than skills – not sure I could repeat what I did.
- My documentation of my steps and procedures was poor, and should have been better to ensure the same issues to not appear again.